"Have I Been Pwned?" is a free service to check if an account was compromised in a data breach: Syncope can use it to make stronger checks on passwords

"Have I Been Pwned?" was created by Troy Hunt as a free resource for anyone to quickly assess if they may have been put at risk due to an online account of theirs having been compromised or "pwned" in a data breach.
From the other side, Apache Syncope allows to define and enforce password policies, as a composition of so-called "password rules", e.g. constraints to apply to password values.
One of the latest chages added to the upcoming Apache Syncope 2.0.9 is the possibility to empower the "Have I Been Pwned?" free service to prevent that a pwned password value is set by an user either during create or update.
In the following, some simple steps to enable the new password rule will be presented.
First of all, a recent Apache Syncope 2.0.9-SNAPSHOT build shall be obtained; for the sake of simplicity, here is a direct link to one of the latest standalone distribution packages. Please refer to the Getting Started guide about how to work with it.
After startup, log into the Admin Console, then go to Configuration > Policies > Password and click on the plus button on the bottom right; a modal window will appear, set "Global Password Policy" as Description, then click on Save.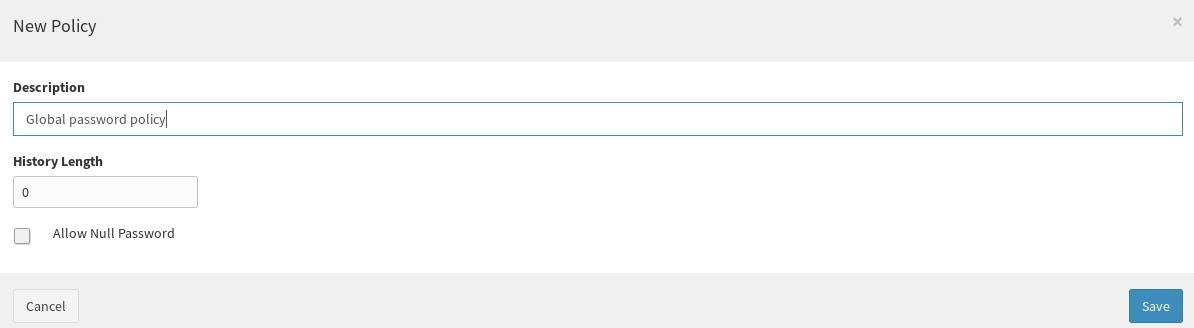
Now click on the table row of the newly created Password Policy, and select "compose" for the pop-up menu; a modal window will appear, click on the plus button, then select "org.apache.syncope.common.lib.policy.HaveIBeenPwnedPasswordRuleConf" from the Type dropbox, give a name to the new rule, click on Next and then Finish.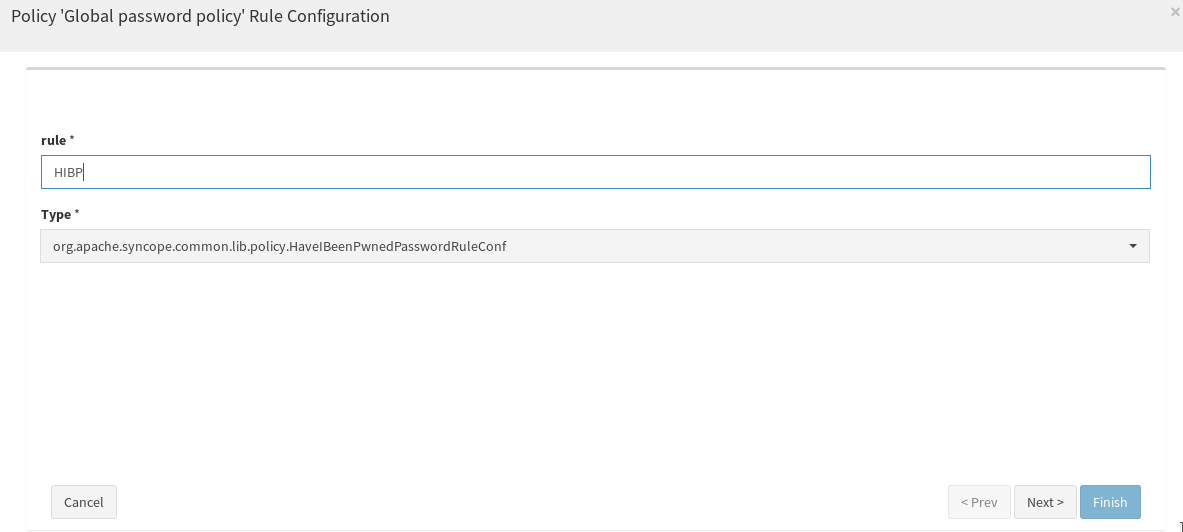
At this point, go back to Realms and click on the pencil icon on the bottom right; a modal window will appear, select "Global Password Policy" for the "Password Policy" field and click on Finish.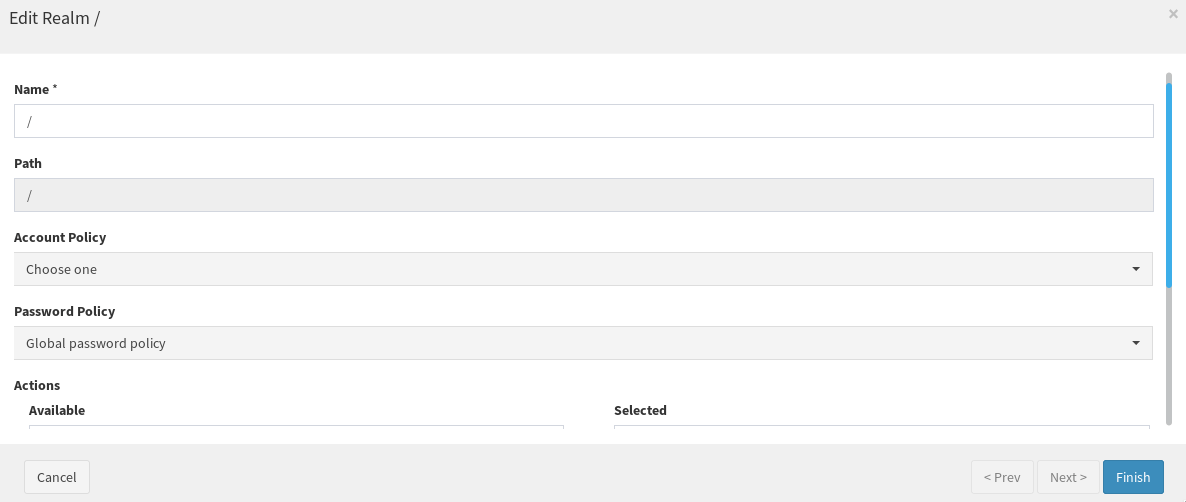
With this last step, the new password policy is configured for all users, as it was associated to the root Realm.
Now, when attempting to set the leaked password values (as the classic "password"), an appropriate error is raised.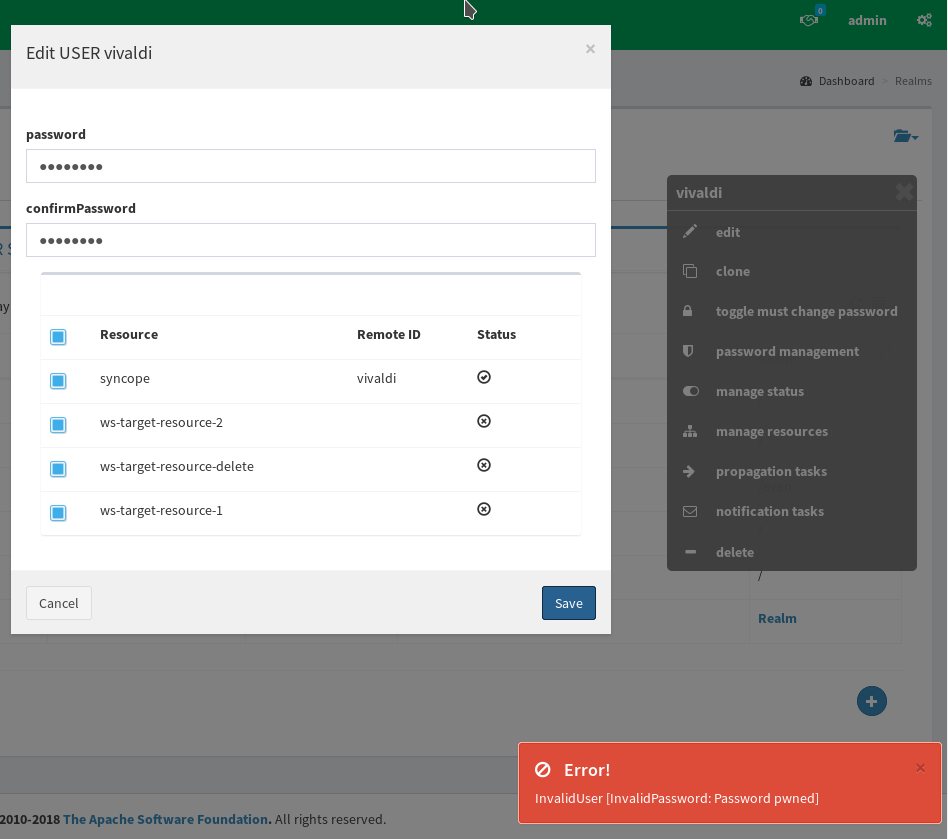
 Good
Good 
