Apache Syncope can manage users on external LDAP directory server since almost the beginning, via ConnId's LDAP connector.
Apache Syncope can manage users on external LDAP directory server since almost the beginning, via ConnId 's LDAP connector .
The release 1.1.0 Ad libitum , however, has extended the capabilities to include role provisioning: for LDAP this means the possibility to manage groups (groupOfNames, groupOfUniqueNames), besides users.
But what does this mean exactly? Think you manage (e.g. create / update / delete / assign) users and roles on Apache Syncope as centralized IdM, and have all these entities automagically kept in sync on your OpenLDAP (or ApacheDS, or OpenDJ, or any other LDAPv3 compliant directory server). Or even the other way round: bring user and group data from external LDAP resource into your friendly Apache Syncope.
Making a successful configuration for all these features might not seem straightforward at a first glance: I am going to provide below a working sample that you can adapt to suit your own needs.
Moreover, the configuration in the following is the same as contained in the Apache Syncope virtual machine demo , hence you can also see it there in action.
Configuration
For any configuration operation, just empower the admin console: it's awesome, it's complete, it's working ;-)
Connector
Apache Syncope 1.1.0 comes with ConnId LDAP connector bundle 1.3.5, so you should already have everything you need.
Go under Resources > Connectors and click the Create new connector button on bottom: a window will appear.
Set the name you like as Display name, choose the Location where your LDAP connector bundle is.
Then move to the Configuration tab and fill only the following fields with the provided data (this assumes that root DN is dc=syncope-idm,dc=org, change it with yours if needed):
| Host | localhost |
| TCP Port | 389 |
| Principal | cn=admin,dc=syncope-idm,dc=org |
| Password | (Principal's password) |
| Base Contexts |
ou=people,dc=syncope-idm,dc=org |
| Password Attribute | userPassword |
| Account Object Classes | inetOrgPerson |
| Account User Name | uid |
| LDAP Filter for Retrieving Accounts | uid=* |
| Group Name Attributes | cn |
| Maintain LDAP Group Membership | true |
| Password Hash Algorithm | SHA |
| Uid Attribute | cn |
| Read Schema | true |
| Base Contexts to Synchronize |
ou=people,dc=syncope-idm,dc=org |
| Object Classes to Synchronize |
inetOrgPerson |
| Status management class | org.connid.bundles.ldap.commons.AttributeStatusManagement |
As you can see, groupOfUniqueNames is used as groups object class: if you want to use groupOfNames instead, be sure to change it in all related fields.
Next, move to the Capabilities tab and check everything.
Finally click the Save button.
External Resource
Move back to the Resources tab and click the Create new resource button on bottom: a window will appear.
Set the name you like and choose the Connector created in the step above.
IMPORTANT: choose org.apache.syncope.core.propagation.impl.LDAPMembershipPropagationActions as Actions Class. This will maintain the association between users and roles on the LDAP resource as defined in Apache Syncope.
After setting user and role mapping as above, click the Save button.
User mapping
You may need to define some attribute schema on Apache Syncope (badge, email, firstname, fullname, surname) before being able to complete the configuration below.
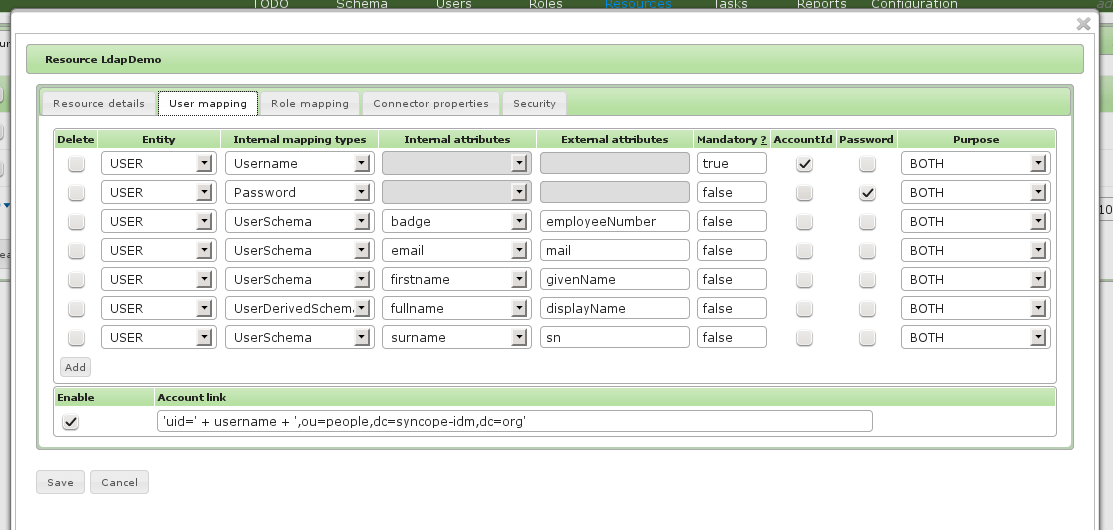
Role rapping
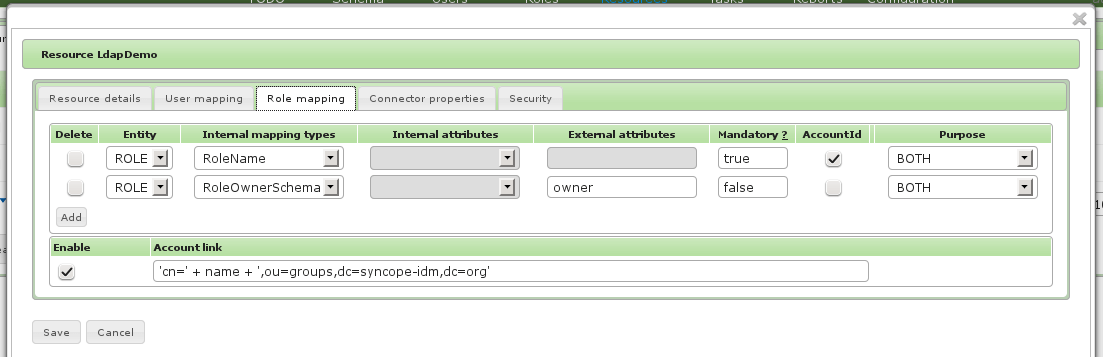
Testing
Propagation
With configuration above Apache Syncope is fully enabled to manage users and roles on LDAP:
- create user user1, fill all required information and give the LDAP resource: you will find the LDAP entry uid=user1,ou=People,dc=syncope-idm,dc=org
- create role role1 and give the LDAP resource: you will find the LDAP entry cn=role1,ou=Groups,dc=syncope-idm,dc=org
- create user2 and assign him to role role1: you will find uid=user2,ou=People,dc=syncope-idm,dc=org among uniqueMember's value of cn=role1,ou=Groups,dc=syncope-idm,dc=org
Synchronization
Some additional configuration is needed for enabling synchronization, e.g. ability to pull data from external LDAP directory server.
Go under Tasks > Synchronization Tasks and and click the Create new task button on bottom: a window will appear.
Set name and description you like more.
IMPORTANT: choose org.apache.syncope.core.sync.impl.LDAPMembershipSyncActions as Actions Class. This will maintain the association between users and roles on Apache Syncope as defined on the LDAP resource.
After flagging any checkbox, click the Save button.
At this point Apache Syncope is fully enabled to manage users and groups from LDAP. First create some sample users and groups in the LDAP directory server, then go back to Apache Syncope admin console and execute the Synchronization Task created above: you will find both users and roles in Apache Syncope, created according to data provided in LDAP.
Changelog
During synchronization, Apache Syncope can query the LDAP directory server in two distinct ways: either the full list of entries (that will need to be parsed in order to catch the actual modifications performed since last run) or just such actual modifications.
As anyone can see, the latter is much more better than the former but its usage is limited due to the fact that the ConnId LDAP connector currently supports actual synchronization operation only from some servers (as Sun Directory Server or OpenDJ).
This fact has an impact on the configuration; if you are running one of supported LDAP directory servers:
- select the SYNC capability for the LDAP connector instance
- unflag "Full reconciliation" from the synchronization task
otherwise
- selecting the SYNC capability for the LDAP connector instance is irrelevant
- be sure to flag "Full reconciliation" from the synchronization task
What's next?
LDAP directory servers are quite common in identity management scenarios, but Microsoft Active Directory is almost as common; I will try to post something similar in a short while: stay tuned!
 Yes, Excellent!
Yes, Excellent!

