Keycloack is an open source Access Management solution by RedHat, aimed at modern applications and services. It supports several authentication and federation standards, including OpenID Connect.
Apache Syncope was recently equipped with OpenID Connect client features, allowing Single SignOn to Admin Console and Enduser UI; in the following, we are going to show how to integrate Apache Syncope with Keyloack, by leveraing the OpenID Connect protocol.
First of all, create a "docker-compose.yml" file. Take this as reference, so that you'll create the full Syncope suite (Core, Console, Enduser) running on a MySQL instance.
Here is a sample "docker-compose.yml" file content:
services:
version: '3.3'
db:
image: mysql/mysql-server:5.7
restart: always
environment:
MYSQL_DATABASE: syncope
MYSQL_USER: syncope
MYSQL_PASSWORD: syncope
syncope:
depends_on:
- db
image: apache/syncope:2.1.0
ports:
- "18080:8080"
restart: always
environment:
DBMS: mysql
DB_URL: jdbc:mysql://db:3306/syncope?characterEncoding=UTF-8&relaxAutoCommit=true&useSSL=false
DB_USER: syncope
DB_PASSWORD: syncope
DB_POOL_MAX: 10
DB_POOL_MIN: 2
OPENJPA_REMOTE_COMMIT: sjvm
syncope-console:
depends_on:
- syncope
image: apache/syncope-console:2.1.0
ports:
- "28080:8080"
restart: always
environment:
CORE_SCHEME: http
CORE_HOST: syncope
CORE_PORT: 8080
syncope-enduser:
depends_on:
- syncope
image: apache/syncope-enduser:2.1.0
ports:
- "38080:8080"
restart: always
environment:
CORE_SCHEME: http
CORE_HOST: syncope
CORE_PORT: 8080
DOMAIN: MasterThen, add a Keycloak instance to have a fully working Keycloak container. E.g.
keycloak:
image: jboss/keycloak:latest
ports:
- "8081:8080"
restart: always
links:
- db
environment:
KEYCLOAK_LOGLEVEL: INFO
KEYCLOAK_USER: admin
KEYCLOAK_PASSWORD: admin
DB_VENDOR: h2
In this example we use "h2" for in-memory database persistence.
Run:
$ docker-compose up -d
to pull, create and start all containers.
Go to http://localhost:8081 and access the Keycloak "Administration Console" with "admin" / "admin" credentials, as specified in the "docker-compose.yml" file.
Create a new OIDC Client on Keycloak
From the Keycloak Admin Console, go to "Clients", click "Create" and fill "Client ID" and "Client Protocol" fields:
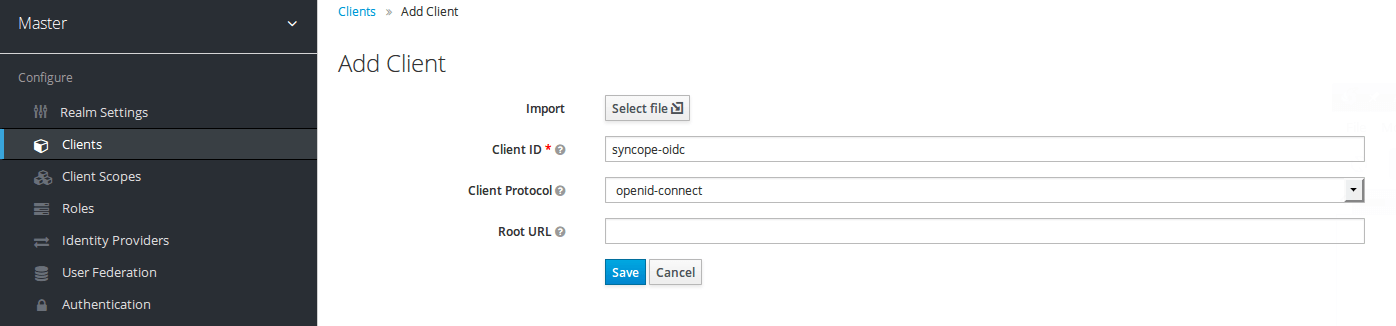
Click "Save" and fill other fields like this:
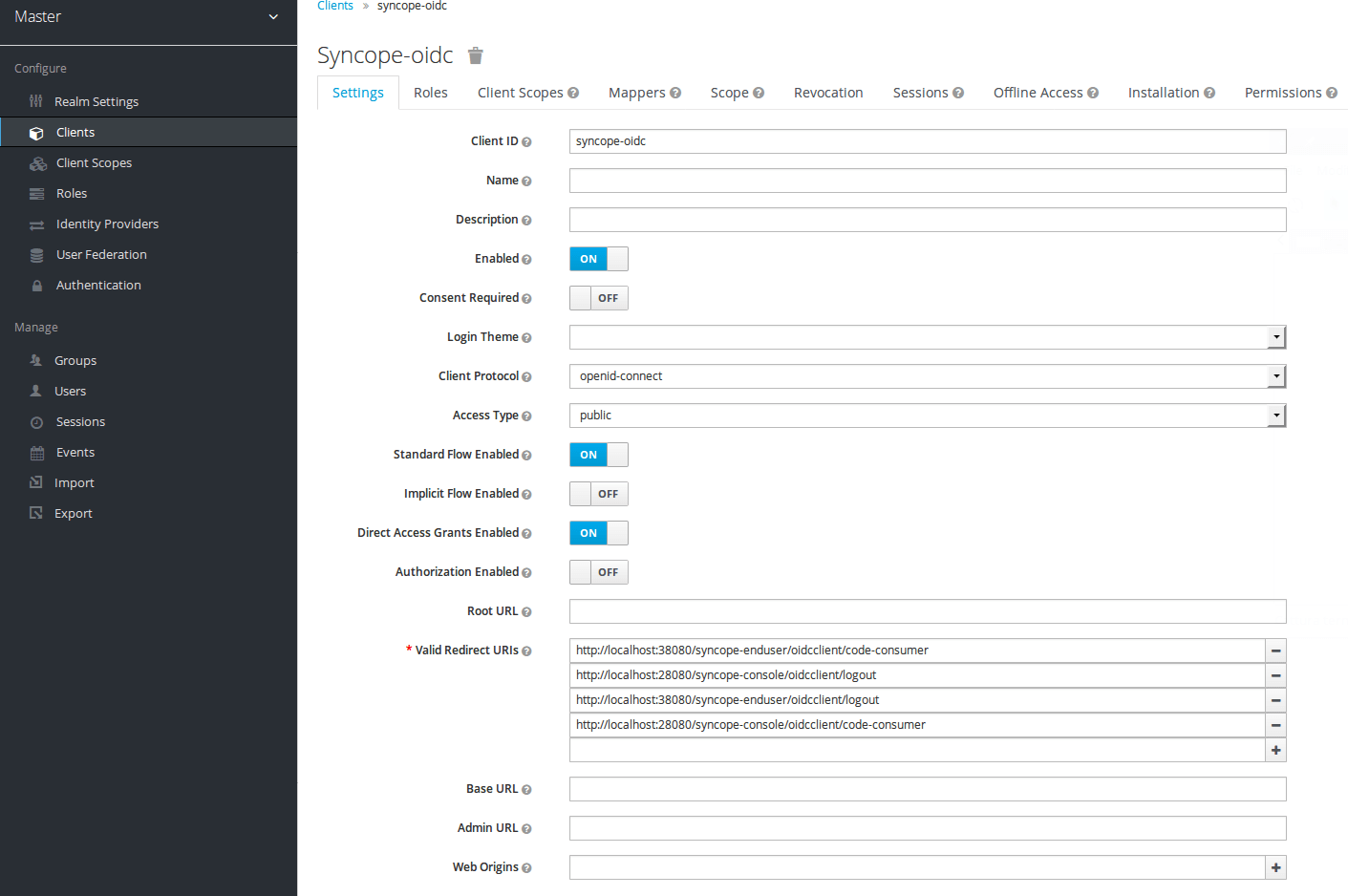
It is important to specify the following entries in the "Valid Redirect URIs" field list:
- http://localhost:28080/syncope-console/oidcclient/code-consumer
- http://localhost:28080/syncope-console/oidcclient/logout
- http://localhost:38080/syncope-enduser/oidcclient/code-consumer
- http://localhost:38080/syncope-enduser/oidcclient/logout
Save the new client!
Now, you need to note down the name of the new created client (the "Client ID"), "syncope-oidc" in our example, and the "Client Secret" token (you can find it in "Clients" -> "account" item -> "Credentials" tab -> "Secret").
Let's now create a Keycloak user that we'll use to access Syncope using the OIDC authentication.
Still from left panel, select "Users" -> "Add User" button and enter something like this:
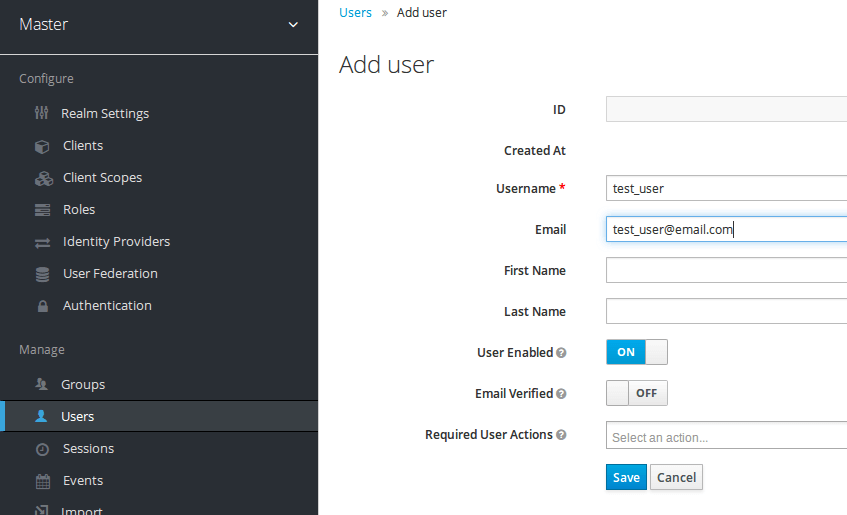
Save the user!
Add a new Syncope OIDC Provider
Go to http://localhost:28080/syncope-console and access the Syncope Admin Console with default "admin" / "password" credentials.
From left panel, select "Extensions" -> "OIDC Client" and add a new OIDC Provider by clicking on the "+" icon.
Here is an example:
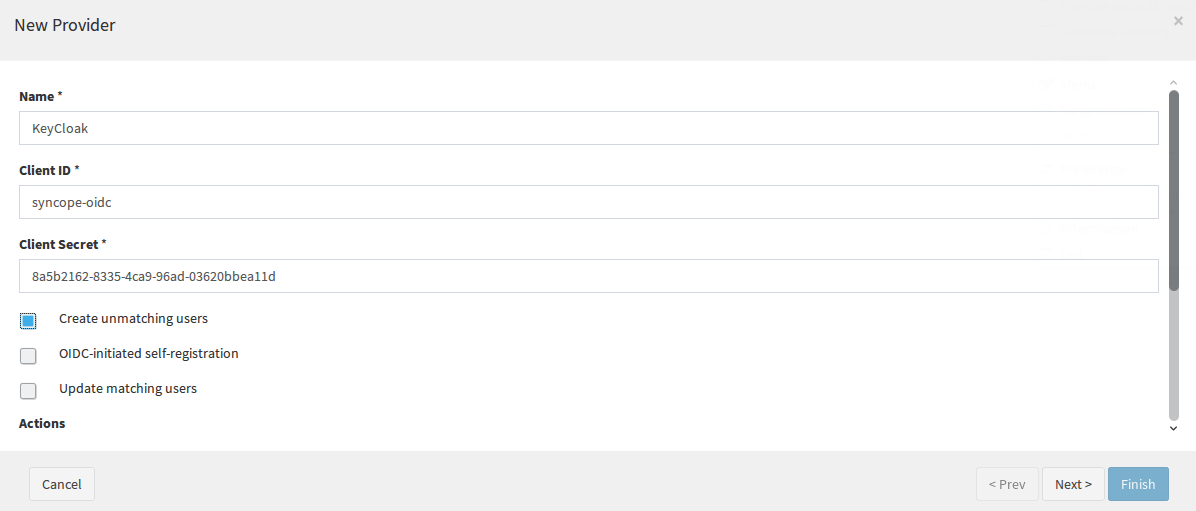
Click "Next", here you need to find the Docker IP of the "Keycloak" running container. Use the following command:
$ docker inspect -f '{{range .NetworkSettings.Networks}}{{.IPAddress}}{{end}}' [KEYCLOAK_CONTAINER_NAME]
Now you can enter http://[CONTAINER_IP]:8080/auth/realms/master (note that the port is "8080" and not "8081"):
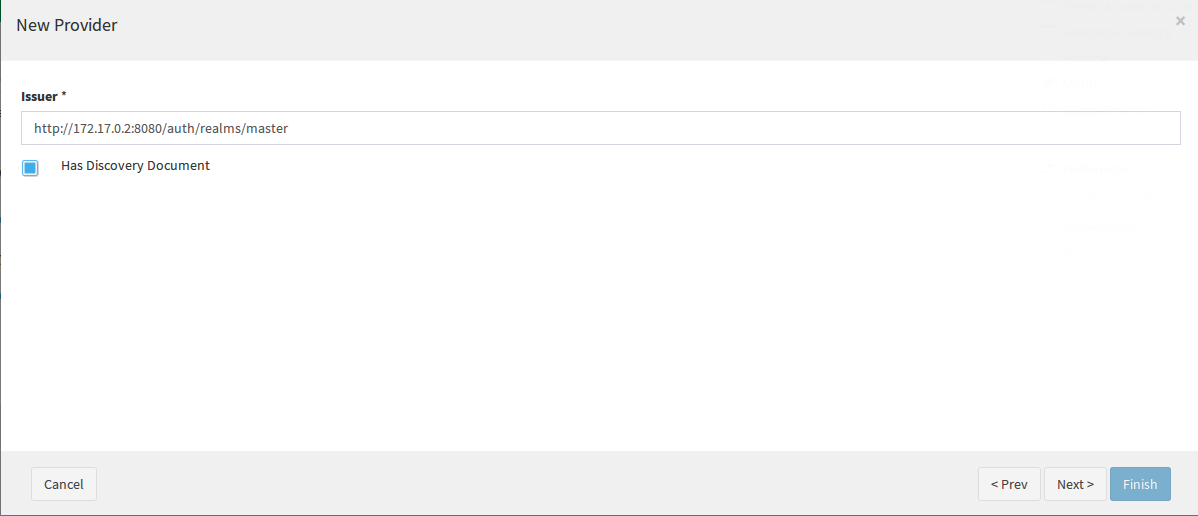 ;
;
It is the Base URL of the related Keycloak realm.
Click "Next" again and enter a mapping for the new created users from Keycloak. E.g.
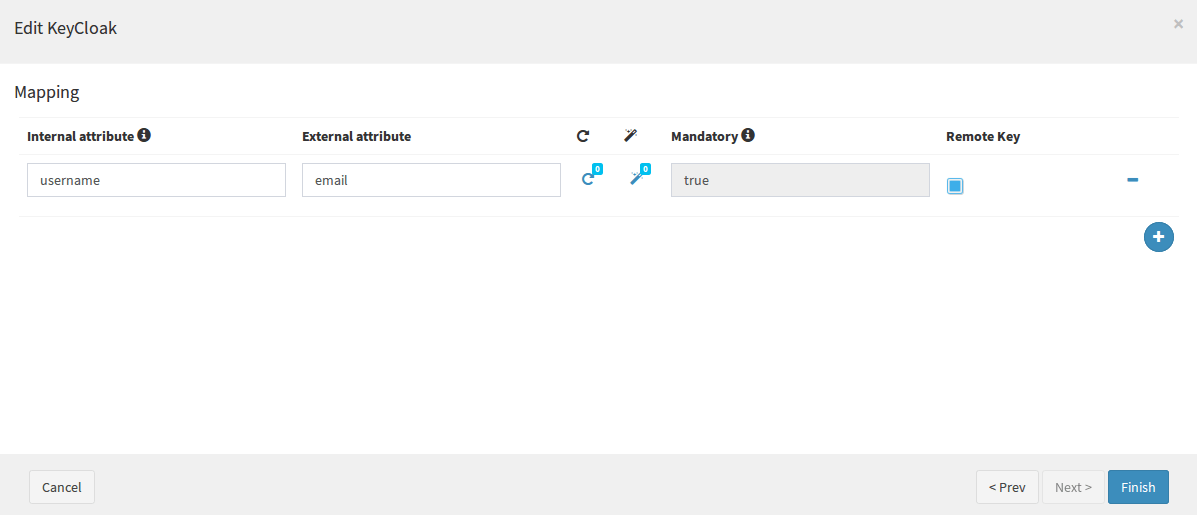
Note that you can use the same method to login to Syncope Enduser ( http://localhost:38080/syncope-enduser)
 Good
Good

